83 percent of enterprise workloads will be in the cloud by 2020, Forbes says. Along with that, 66 percent of IT professionals claim that their biggest concern related to the adoption of cloud computing services, is security. What do you as a cloud customer can do to protect your business? Read our article below for the details.
written by:
Veronica Chizh
83 percent of enterprise workloads will be in the cloud by 2020, Forbes says. Along with that, 66 percent of IT professionals claim that their biggest concern related to the adoption of cloud computing services, is security. What do you as a cloud customer can do to protect your business? Read our article below for the details.
Picture an imaginary situation in which Marc Lucky is the key figure. Marc Lucky is a Chief Information Officer (CIO) at the Wonderful Big Company, LTD (WBC). The WBC has been offering high-quality business software for years and now it’s considering a new niche, a Software as a Service (SaaS). The industry is growing by leaps and bounds: as Marc has found from the IDC’s study, SaaS will account for about 60 percent of public cloud spending by 2020. Gaining new customers by providing high-quality in-demand services will bring new revenues for the WBC. Marc’s company will stick to its core competency (i.e. business software), and a Cloud Service Provider (CSP) will assist the WBC with hosting solutions, namely Infrastructure as a Service (IaaS). However, what may seem a lucrative offer on paper, when being implemented, poses new grave challenges for the WBC. For Marc, in particular, it is cybersecurity threads that clouds carry in themselves, as 66 percent of IT professionals claim that their biggest concern related to the adoption of cloud computing services, is security.
If stakes are so high, why take the risks at all? As it happens, using cloud computing services is as beneficial as it is risky.
CaaS offers:
- Rapid scalability;
- Pay as you go capabilities;
- Extensive resource availability.
Thus, to take well-balanced decisions, Marc indulges into a thorough risk assessment campaign.
Spooky stories to tell in the dark
Marc starts from studying failures.
Plain as it may seem, learning from others’ failures may save you many troubles. There’s nothing disreputable in taking notice of big players’ mistakes. This statement is backed by Rich Petersen, co-founder and president of JetStream Software, commenting on Cisco’s data loss incident. “Our focus is on the loss of data, so we see important lessons in incidents like the Meraki data loss in August of 2017, when on-premises systems failed to back up data to the cloud service as it was designed to do,” – he says.
DXC’s is the next case to consider. A DXC programmer involuntarily uploaded the company’s private AWS keys to Github. The resulting breach incurred the company over $64,000 in loss before it was fixed.
Cloud provider Nirvanix went bankrupt in 2013 and gave its former customers two weeks to retrieve their data before the company shut down its servers. Many of the affected companies managed to do the things in time, although some SME customers had too much data stored on Nirvanix’ servers to cope with the task. Later on, Nirvanix went into the arrangement with IBM and offered its former customers to shift their data via high-speed connection. However, this was the only option available, and for those former Nirvanix’ customers willing to make use of Google’s, Microsoft’s or Amazon’s services or switch to any other provider, Nirvanix rendered no assistance whatsoever.
From words to actions
The mentioned above cases take up only a page in the solid volume of cloud crashes. Once a potential CSP’s customer realizes that being on a cloud is not a ‘one time drop and forget’ process, he/she starts doing extra to reinforce his/her data security. In his article, Sam Bocetta, independent journalist and security analyst, recommends conducting on-prem audits before deploying security measures. Hence, Marc’s next step is to scrutinize his own company’s premises, i.e. software, hardware, storage. This will help Marc take a well-informed security solution based on his company’s strengths and weaknesses.
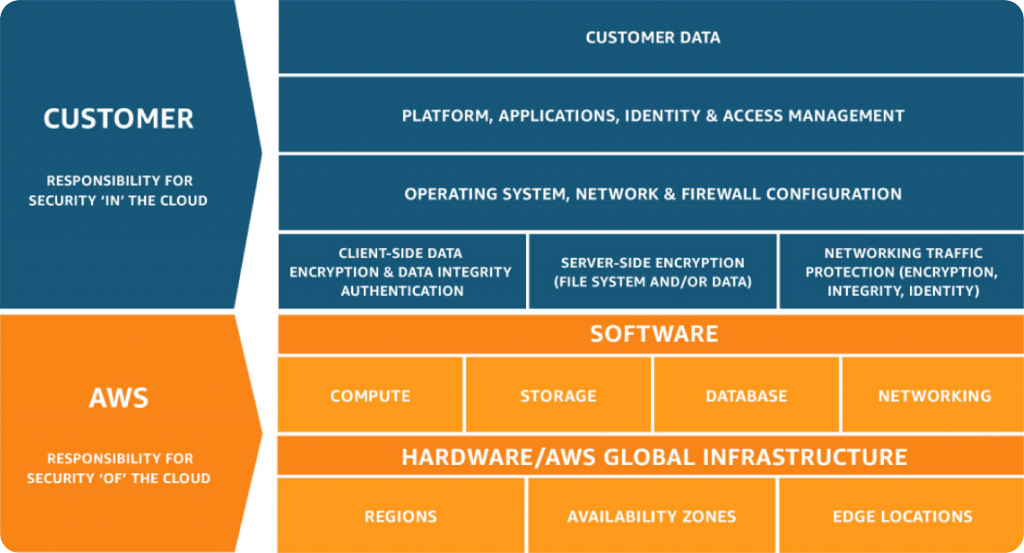
Thus, Marc is now well aware about his company’s strengths and weaknesses and opts for specific security solution from a given CSP. Does it mean that cloud security issues will never touch upon the WBC? Time to party hard and rest on laurels? Ha. “Security and Compliance is a shared responsibility between AWS and the customer", - that what AWS, a leading cloud computing services provider, says on the subject. Amazon articulates clearly how far its security efforts stretch (see the table below or study the details here). It means Marc still has a lot on his plate.
Source: aws.amazon.com
Identity and access management
Anyone wishing to gain access to the airport’s security system could buy the privileged credentials on the Dark Web for as much as $10 last year, according to McAfree. Forewarned is forearmed, an old proverb says. Therefore, Marc chooses to be proactive in ensuring the WBC’s security. First thing on his to-do list is to arrange a reliable identity and access management in cloud environment. Hence, to reinforce the protection of the WBC’s systems, Marc can introduce numerous authentication options. He is free to deploy a single authentication mechanism (log-on credentials, multifactor authentication, third-party authentication, simple text passwords, 3D password objects, graphical passwords, biometric authentication, digital device authentication) or leverage the combination of the listed mechanisms.
Better visibility
Next to do is gain a better visibility of cloud services and data. Marc is pretty knowledgeable about the tools and technologies that can provide a 360-degree view of his company’s cloud environment. These may be Amazon CloudWatch for the AWS clients. Riverbed’s AppResponse and AppInternals are great third-party tools that can be deployed in the cloud. Visibility Platform by Gigamon’s ensures even down to a packet-level visibility. Greater visibility will allow the WBC to react to incidents faster and gain higher confidence in embracing transformative cloud services. Now Marc’s informed what the WBC’s data goes to the cloud and where it is stored.
Data encryption
CSPs often ensure adequate data encryption. Although, however trustworthy the CSP may be, Marc is going to deploy a sophisticated encryption solution before sending data to the cloud. The encryption keys will be kept on a separate server or a storage block, with a keys backup located offsite for safety purposes.
However, there should be a distinction between the corporate data requiring encryption and the data that can be very well stored in plain text. With this regard, Marc establishes clear rules for information classification and informs thereof all the IT staff provided with an access to the cloud.
Staff coaching
However cautious management can be, ensuring security is a company-wide objective. That means that all the personnel should undergo relevant security coaching. For the developers and IT staff it can be OWASP Top 10 or Cloud Controls Matrix, while for a non-IT staff Marc is going to arrange relevant courses such as Employee Skills Training Platform by Kaspersky lab or Cyber-Security Fundamentals For Non-IT Staff by Digital Assure Limited, etc. Along with formalized quarterly training, security team will employ constant reminders for the WBC’s employees, thus reducing the risk of malware in a cost-effective manner.
Automation
Besides adding a bit of the responsibility burden, will the WBC’s people be otherwise affected by deploying cloud computing services? Largely, things will stay the same for the professionals engaged in the company’s core competency. Moving to the cloud will demand as much learning from them as mastering a new framework. For the information security staff, however, ensuring the network stability will imply adding more automation to the processes. The less human element is left, the fewer incidents can be expected. “Automation, once perfected, never deviates from the rules that have been defined; therefore, they never miss a step or leave a door open,”- Sam Bocetta highlights.
Talent acquisition
And surely, automation yields best results if orchestrated by an experienced cybersecurity expert. However, to find one has become a real challenge for many companies. According to Cybersecurity Ventures, there will be 3.5 million unfilled cybersecurity positions by 2020.
“Should you come by an adequately trained specialist, grab and hold him/her,” – Marc says to the HR team. He will never regret this decision later on.
Penetration testing
Hopefully, in case Marc is hesitant whether he made his every best effort to protect his system, he can double-check it, say, through penetration testing. Penetration testing will disclose hidden flaws and vulnerabilities of the system under test, thus, allowing the hosting company to get better prepared for real life attacks. At the same time, for multitenant clouds, i.e. those shared by multiple companies, pentesting should be performed in compliance with the restrictions posed by the CSP. In other words, Marc can pentest the WBC’s system only to the extent that other companies’ data is not affected, as allowed by the provider. See the pentest requirements of Microsoft Azure or AWS as an example.
Summing it up…
In the end, if Marc Lucky, the WBC’s CIO, was a real figure, he would do much more to ensure his company’s data is safe once moved to the cloud. Surprisingly, many cloud players do not consider performing even the minimum requirements mentioned above. Keep in mind, that a cloud provider may fence its liability for any possible data breach and will do it legally. A lengthy servicing contract is all too often excessively boring to study. Thus, there are many issues that in your opinion should be covered by the cloud provider. In reality, they are entirely your responsibility. A good piece of security and compliance is exactly the case.
Qulix Systems has extensive expertise in cloud services and is ready to render any assistance you may need to move to the cloud safely. For more information contact our Support team or visit our website.

Contacts
Feel free to get in touch with us! Use this contact form for an ASAP response.
Call us at +44 151 528 8015
E-mail us at request@qulix.com